Home Lab - Design
Hello guys and welcome back in my blog! In this post I would like to share with you how I decided to design my home lab!
Home Lab - Small Recap
I don’t want to annoying you so if you want to read the reason why I decided to buy a server, check my first home lab post
TL;DR:
- Vendor: DELL
- Model: R630 (10x SFF 2.5")
- CPU: 2x E5-2690 V4 (14C and 28T each, total 28C and 56T)
- RAM: 288GB DDR4 2400 MHz
- PSU: 2x 750W
- Storage: 1x 256GB SSD for Hypervisor, 1x 2TB SSD for VMs
- Remote Access: iDRAC8 Enterprise
Connectivity
The server is located in a garage and I do not have the ability to bring wired connectivity to this location. For the past few months I have been running connectivity with some Wi-Fi extenders from my house to the garage, but it is not stable and I decided to improve it.
I recently upgraded my Internet connectivity and changed ISPs; the new ISP (Vodafone) will provide me with an additional SIM with 50 GB included in the FTTH offer. Okay, so what?
Well… I decided to buy an LTE router and install the Vodafone SIM in it. Why? To save a few euros and not have another SIM. This one is already included in my plan, so I don’t need to buy a new one. Essentially Vodafone provides this SIM because if local Internet access is compromised, you have a SIM available and can use the Internet with it. In case of a failure, the 50 GB limit is removed and the SIM becomes an unlimited data SIM.
Okay, now that we have connectivity we need a router to use it. I choose AVM FRITZ!Box 6820 V3 LTE because I already have a FRITZ!Box at home and I can easily set up a VPN between two or more sites. I have always been comfortable with AVM FRITZ!Box in terms of stability and OS, so I see no reason to change
So the final configuration is: SIM + LTE router with IPsec tunnel with Home router 😊
Is it the perfect solution? Is it the more stable internet connectivity solution? Of course not. But it’s what I can do in my infrastructure right now. Hopefully in the future I’ll have a better place to locate the server 😉
Hypervisor
I’m happy to announce that I’ve decided to install VM… nnaaaaahhh!!!! I installed Proxmox in my home lab server.
Why? Well, it’s free ( Broadcom, do you know this word?), open source and it allowed me to learn new skills and test different products. In the end we’re all nerd, we want to test and learn 😉
To be honest the primary idea was VMware, because I worked with it and I know ho to perform standard tasks…. but ehi, no more free license so…. Proxmox is fine 😊
If you want to learn more about Proxmox, here is the website: https://www.proxmox.com/en/
Feedback from a Network Engineer that is able to survive and perform basic/medium task with VMware: networking part is different and I’m still learning it. VM deployment is very easy. You can download remote ISOs directly from Proxmox with a few clicks. New Datastore is easy to add (I’m using local disks, not remote storage). HA, Cluster, Backup and all the other cool features available not tested yet.
I’m not a System/Virtualization Engineer, I just want to run my VMs so the setup is very very simple in my Environment…. you will see it in the next post!
Virtual Machines
In this section I’ll show you a list of Virtual Machines that I would like to install in this first phase. As you already know, VM will likely change during the days and it’s not a problem. The flexibility to have your own server is that you can create/delete as many VMs as you want (keep in mind hardware limitation as CPU, RAM and Storage).
Here is the list:
| VM | Note |
|---|---|
| OPNsense | It will be my firewall and router in the virtual infrastructure |
| Ubuntu Server | A linux machine is always helpful (test env, automation, improve my bash skills and more) |
| Windows Server | well…why not? it can be always helpful as well |
| NetBox | IPAM for my infrastructure. I would like to test and create some script to automate the import of data |
| TIG Stack | Telegraf/InfluxDB/Grafana, probably with docker. Monitoring of the infrastructure |
| eve-ng / CML | I’m considering to purchase both license during black friday, let’s see the budget |
| Nexus Dashboard | I want to play with NDFC and other services |
| ACI Simulator | I know all the limits about this VM, but it can help me in test ansible playbook, python scripts and more without using public sandbox |
| UCSPE | Vm to test UCSM and other cool datacenter products |
Then, I’ll install for sure the Cisco Catalyst SDWAN Controllers (Manager, Controller, Validator) and some C8000v to test the solution.
Moreover, I would like to add a packet inspector, do you have any suggestions for it? Please drop me a message on LinkedIn
or send me an email
, thanks!
This should be the baseline, then everything can be changed, added or removed.
Networking
Now that we have chosen physical server, the hypervisor, the connectivity and we decided which VMs install in our infrastructure, it’s the time where we design the networking part.
First of all, on key concept in my environment is that the OPNsense VM, which is our firewall and router, will be the default gateway of ALL the VLANs created and the IP address will be 172.16.XXX.254/24 in each LAN sub-interface, where XXX is the VLAN ID.
172.16.0.0/24 is the subnet between LTE Router, iDRAC, OPNsense and Proxmox
In this moment will create the following VLANs:
| ID | NAME | NETWORK |
|---|---|---|
| 11 | SERVER_1 | 172.16.11.0/24 |
| 12 | SERVER_2 | 172.16.12.0/24 |
| 13 | SWICH_OOB | 172.16.13.0/24 |
| 14 | SWICH_INB | 172.16.14.0/24 |
| 21 | SDWAN_VPN-0 | 172.16.21.0/24 |
| 22 | SDWAN_VPN-512 | 172.16.22.0/24 |
| 23 | SDWAN_INET-1 | TBD - I would like to use fake Public IPs |
| 24 | SDWAN_INET-2 | TBD - I would like to use fake Public IPs |
| 25 | SDWAN_MPLS-1 | 172.16.25.0/24 |
| 26 | SDWAN_MPLS-2 | 172.16.26.0/24 |
The OPNsense is the default gateway with .254 IP address for each subnet.
VMs will have one or more vNIC based on the requirements.
Remote Access
How do I access my infrastructure remotely? Well… there are multiple ways to access an infrastructure remotely, my choices are… Traditional VPN and Tailscale !
Traditional VPN: With AVM FRITZ!Box you can easily setup a Wireguard VPN. It’s very very easy and you can just follow the wizard from router GUI.
I configured the Wireguard VPN on my home router router becuase it’s the only one with public IP (dynamic) and I’m using a DNS entry as remote endpoint.
So from my mobile or laptop I can just open the VPN client, connect at home and I can reach both home network and lab networks (they are reachable via the IPsec tunnel between home and lab routers).
Tailscale: Tailscale is a VPN service that simplifies secure connectivity between your devices and applications, regardless of their location. It uses the open-source WireGuard protocol to create encrypted point-to-point connections, ensuring that only devices on your private network can communicate with each other.
One of the main advantages of Tailscale is its zero-configuration setup, which means it automatically handles complex network configurations, making it very user-friendly.
Tailscale’s route server functionality allows you to control how network traffic is routed within your Tailscale network, known as a tailnet. This includes features like subnet routers and exit nodes.
-
A subnet router acts as a gateway, allowing devices on your tailnet to access devices on a physical subnet without installing the Tailscale client on each device. This is useful for connecting devices like printers or legacy systems that can’t run the Tailscale client1.
-
Exit nodes route all your internet traffic through a specific device on your tailnet, which can be useful when accessing untrusted networks or services restricted to certain geographic locations2.
These routing features help you manage and secure your network traffic efficiently, providing flexibility and control over how devices communicate within your tailnet. In my setup, I’ll install Tailscale into OPNsense and I’ll configure it as Subnet Router in order to reach all the VMs and applications behind it.
In the end we can say that Tailscale is particularly beneficial for developers, small businesses, and enterprises looking to securely connect remote devices without the hassle of traditional VPN setups
Which one I’ll use?
Probably both! The cool thing is that VPN access depends on Home Internet connectivity, Tailscale depends on Lab Internet Connectivity. So I should be able to reach the lab infrastructure with two different paths.
Diagrams
Finally, I created a small Drawio diagram to document the infrastructure and show you how logically is defined (nothing special):
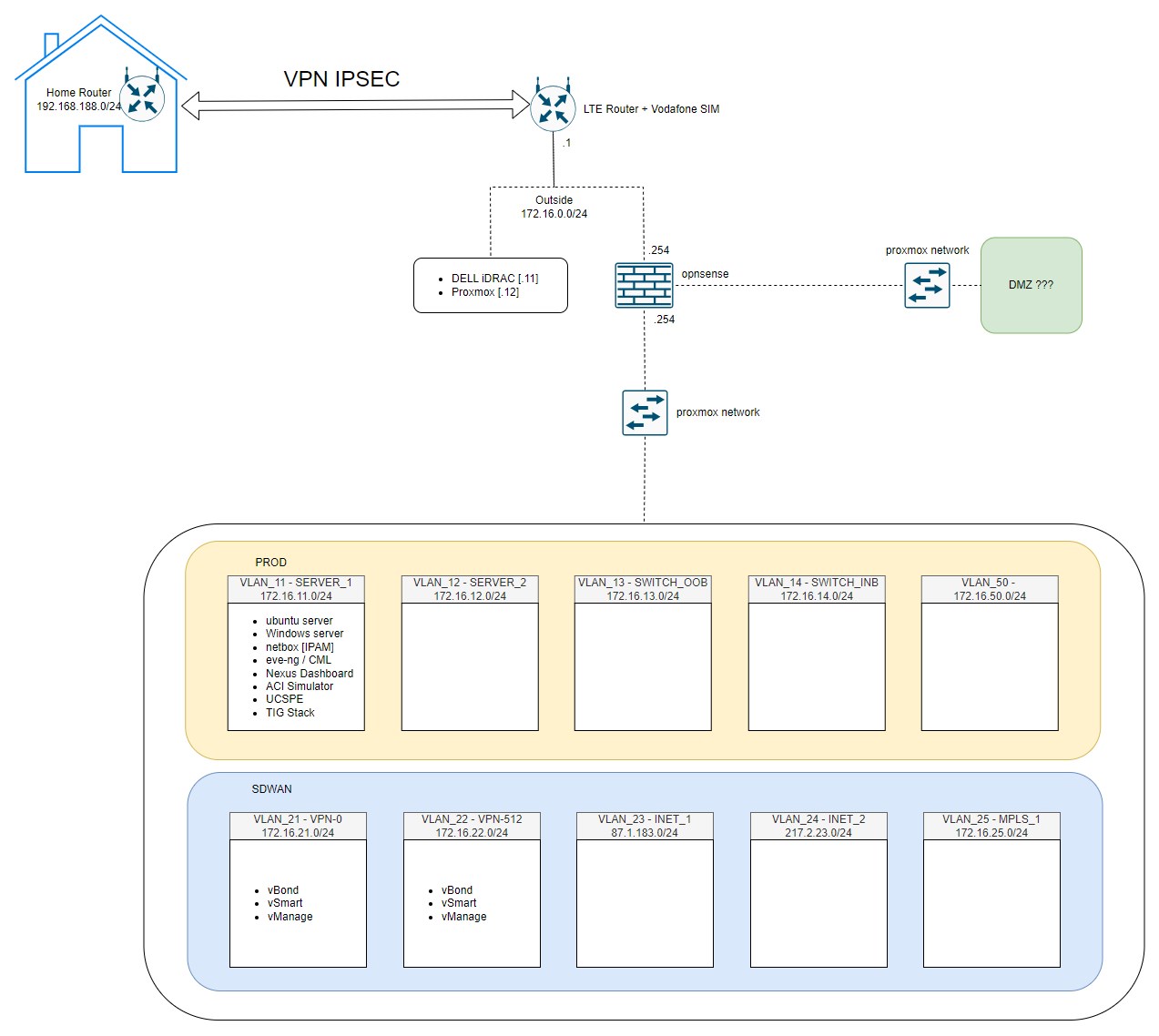
Of course it’s not detailed, of course it’s not a super design or something incredible, but it’s enough for me to proceed and do whatever I want.
If you read all the post, please provide me a feedback with improvement suggestions and more!
Next step? Let’s install Proxmox together!
FTTH Connectivity Flex
My Laptop with 1G LAN Connection to home router after FTTH Upgrade:
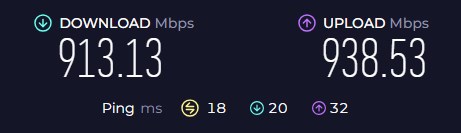
Thanks for your time I hope that you’re enjoying my blog!
If you have some questions, please drop me a message through social networks!😊
👈 You can find the relative icons here on the left of the page
Riccardo